Ridesharing service Uber admitted to a breach of its internal network late last week, with the hacker purportedly gaining access to Uber’s source code, email, and other systems like Slack. The company then soon reassured the public that no customer data was compromised—a claim that not all security experts find plausible.
You should of course still change your Uber account credentials and verify you’re not using that former password anywhere else; it’s an easy and wise precaution to take, as the company’s history includes covering up a major customer data breach for about a year. But that’s not the major takeaway from this incident.
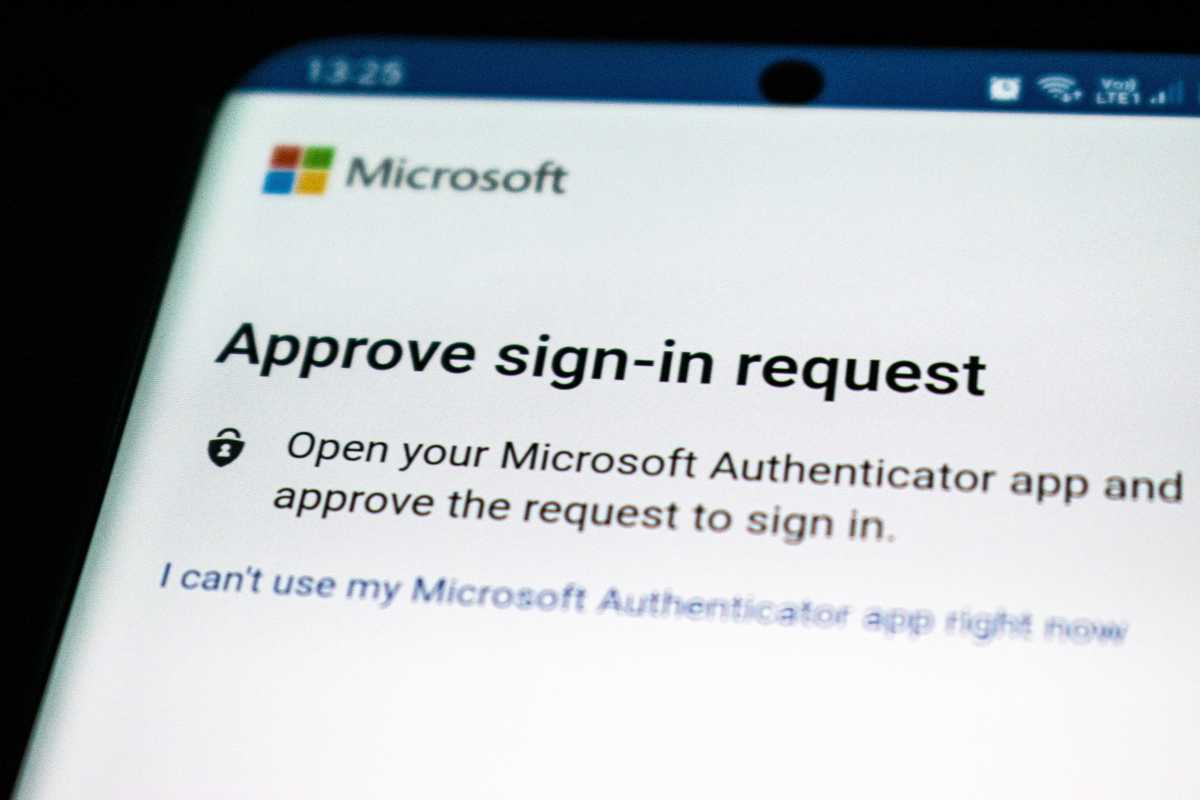
The hack is being reported as the result of social engineering—and overrode security measures that included two-factor authentication (2FA). An employee with a compromised password was spammed with 2FA authentication requests, one of which was finally approved after the hacker posed as an Uber IT person and contacted the employee over Whatsapp.
This outcome doesn’t mean pairing a strong, unique password with two-factor authentication isn’t effective. Only that social engineering is incredibly potent, preying on easily made mistakes. In fact, this latest Uber breach highlights three key ways you can better protect yourself online.
1. Always stop and think
Ed Hardie / Unsplash
A password is your first line of defense against unauthorized access to your online accounts. Two-factor authentication is the second layer of defense, in case your password becomes compromised.
If you choose a form of 2FA that sends requests to your phone or an app on your phone, authorization requests should only pop up when you successfully enter a password.
You. No one else. The website or app itself has system permissions to access your account(s) and all the activity you’ve performed on them without ever involving you. (So does your IT department for work-related accounts, for the record.)
You should only see a 2FA authorization request come through when you’re in the middle of logging into an account. If not, you’ve got a problem—especially if you’re getting all but spammed with multiple requests.
So your third and final layer of defense is your sharp, active brain. Be wary of unexpected 2FA requests. They’re absolutely fishy (that is, “phishy”).
2. Know who to trust
Markus Spiske / Pexels
Account access should be only available to two entities: You and the company running the website, service, or app. And as mentioned above, that company doesn’t need you to access your account. Always rule out communication requesting your password or two-factor information as fraudulent.
Once you’ve received a two-factor authentication request out of the blue, that’s your cue to call in reinforcements. Contact the website or app’s customer service immediately. You want to report the unauthorized use of your password, and receive guided assistance in resecuring your account.
(You might be tempted to change your password immediately—not a bad instinct, but you’ll usually need to pass a two-factor check for it to go through if 2FA is active. If you have only this one method for 2FA, and your hacker is sending multiple requests to your phone, you could run the risk of accidentally approving your would-be hacker’s request instead of the one you generated.)
3. Pick a resilient form of 2FA

Yubico
The more convenient your form of authentication, the easier to compromise. This axiom applies as much to two-factor authentication as, say, password length.
Password length gets discussed way more often, because it’s the first line of defense and often the only line of defense. Tech journalists and security experts often sigh in relief when people use any form of 2FA at all. But two-factor authentication methods vary in how resistant they are to hacking and human error:
- Email and text message are simple and easy to understand, and you can often access them from multiple devices. However, they also rely on unsecure communication. These types of accounts can be taken over via social engineering, too.
- Devices (e.g., smartphones or tablets) and apps that receive push requests are an improvement over email or text, and moving the 2FA setup to a new device (when needed) is usually easy. But they’re still weak against human fallibility, like a mistake when swiping or tapping on a phone screen, or social engineering.
- Apps that you have to open manually to view a 2FA code should only be viewable to you—a big plus. However, this level of security only applies when codes are only accessible locally on the device, not when stored and synced via cloud storage. The downside is that if you don’t back up your setup, restoring access to your 2FA codes can be a royal pain.
- Hardware tokens are completely independent physical items that can generate and display a 2FA code for use, or handle the 2FA authorization seamlessly via a USB port or a wireless connection (NFC or Bluetooth). As you can imagine, these are very secure, but run the risk of being lost. (You’ll usually need more than one for safety.)
In short, if you know you’re likely to be more susceptible to social engineering (or are at risk for more attempts at social engineering), pick a method that covers your rear if you have an off day. Just be sure to protect yourself against logistical headaches, too—which are likelier with more secure forms of 2FA. For even more protection tips, be sure to read our guide to 5 easy tasks that supercharge your security.






