Google Authenticator first launched in 2010, and the app—which stores and generates two-factor authentication (2FA) codes—lacked backups and multi-device support for years. It made transferring phones more difficult, and dealing with a lost or stolen device a complete nightmare if you didn’t have an alternate form of 2FA in place. You’d be missing the info needed to log into accounts protected by that extra layer of security and end up locked out.
On Monday, that situation finally changed when Google updated Authenticator with support for cloud-synced backups. As of version 6.0 on Android and version 4.0 on iOS, you now have the option to back up your 2FA seeds (the information that codes are generated from) to a Google account. If you choose to do so, you’ll be able to access and manage your 2FA codes from any device.
It’s a feature Google Authenticator users have requested for ages, and for good reason. Account lockouts are no joke. But even with such a hellish scenario in mind, you may want to still hold off syncing your 2FA codes in the cloud.
At the moment, Google Authenticator backups don’t use end-to-end encryption (E2EE)—and as pointed out by the security researchers who discovered the issue, your 2FA seeds don’t remain completely secret. Google has the ability to see them.
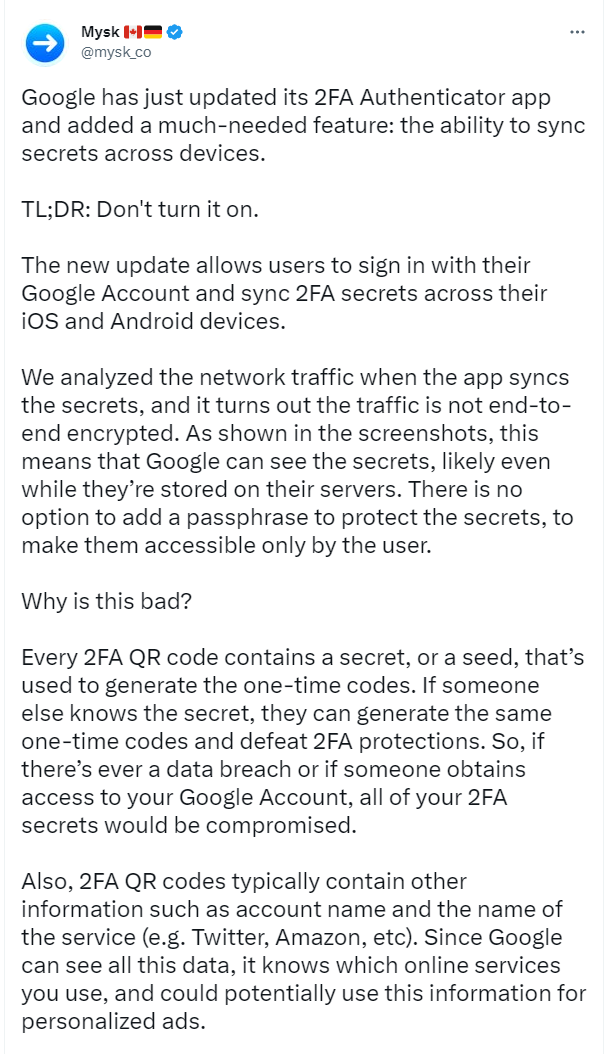
A partial screenshot of the warning tweeted out by Mysk.
PCWorld
Why is that the case when Google says it uses encryption in transit (when you’re sending info to and from its servers) and at rest (when the data sits on its servers)? It relates to how the data is encrypted. With the current method, Google holds the encryption keys—and because it has the ability to encrypt and decrypt your data, it can see the info when it’s unencrypted.
In contrast, if your Google Authenticator 2FA seeds were secured with E2EE, you’d control the encryption. Your data would remain secret when leaving your device, passing between different servers, and stored on Google’s servers. In practical terms you’d lock down the 2FA seeds on your phone with a passcode or password, and then use the same credential to unlock them anytime you downloaded them to a new device.

Keep it secret. Keep it safe. (This is just one 2FA account stored in Google Authenticator. You can have more.)
PCWorld
E2EE better shields you if your Google account (or more catastrophically, Google’s servers) becomes compromised. Think of it like leaving a set of important house keys in a safe deposit box. In theory, they’re safe—so long as you never lose your safe deposit box key and no one makes a duplicate unbeknownst to you (i.e., someone discovering or guessing your Google account password). You also have to trust the bank employees won’t access them, and will always properly safeguard the vault holding the safe deposit boxes.
But since someone can steal your safe deposit box key (so to speak—people often reuse passwords or use weak ones), you can get more protection by first wrapping and sealing those house keys in a way only you can undo. (This is E2EE.) You could get carjacked on the way to the bank, or the bank could have an employee go rogue, or someone could blow up the vault with safe deposit boxes, but your precious keys would remain secure.
According to Google, however, the lack of E2EE support is intended. Christiaan Brand, the group product manager for the Authenticator app, explained in a short series of tweets that the team balanced protection with usability and convenience. Brand also revealed optional end-to-end encryption would eventually make its way to Authenticator.
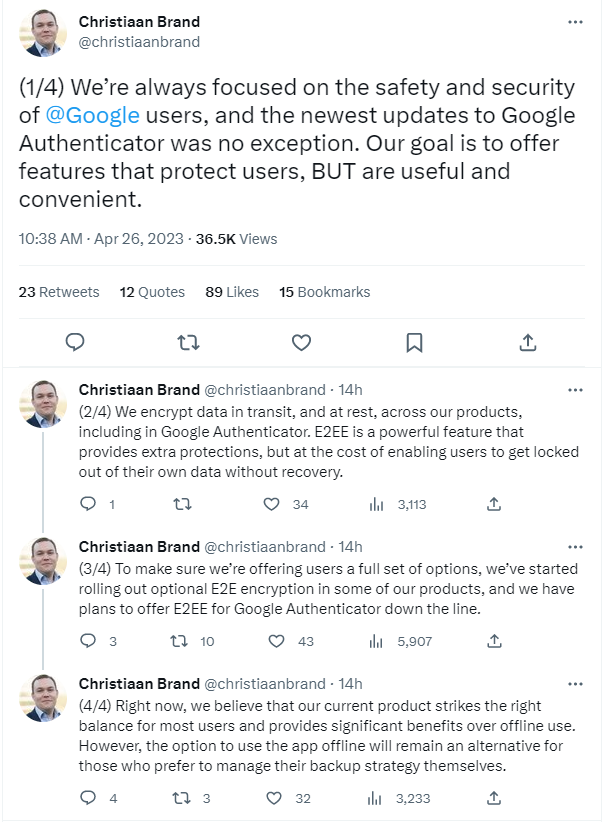
PCWorld
Until then, you should probably consider holding off on backups for Google Authenticator. The risk might not be worth the reward—not when you can switch to a better alternative app. For cloud-synced 2FA codes, Authy has cross-platform support (iOS, Android, Windows, Mac, Linux), uses E2EE, and also lets you to restrict the addition of new devices.
Meanwhile, if you only need to back up your 2FA seeds, you can use an app like Aegis (Android) or Raivo (iOS). It supports password protection and encryption of your 2FA secrets. You don’t have to save to the cloud, either. Instead, you can export an encrypted copy of your seeds and then store them elsewhere offline.
Aegis / PCWorld
If you choose to still use Google Authenticator’s cloud backups, be sure you have two-factor authentication enabled on your Google account. You don’t want someone with unauthorized access to download Authenticator, link it to your Google account, and immediately see all your 2FA codes—likely the final piece of the puzzle needed to take over your other, non-Google accounts.
Currently, Google’s help pages say that 2FA is mandatory to use Authenticator, so you might think you’re all set if you’ve got cloud backups set up. However, we were able to link Google Authenticator with Google accounts lacking 2FA protection, which contradicts the help pages. (We reached out to Google on the discrepancy, but did not immediately receive a response to our request for comment.) So check and be sure.
Overall, the basic takeaway is that to keep your 2FA codes completely safe, you’re currently best off switching away from Google Authenticator. (You can do so very easily if you follow Google’s instructions for generating an export QR code.) Otherwise, you should at least make sure two-factor authentication enabled for your Google account—and use several 2FA methods to avoid an accidental lockout.




