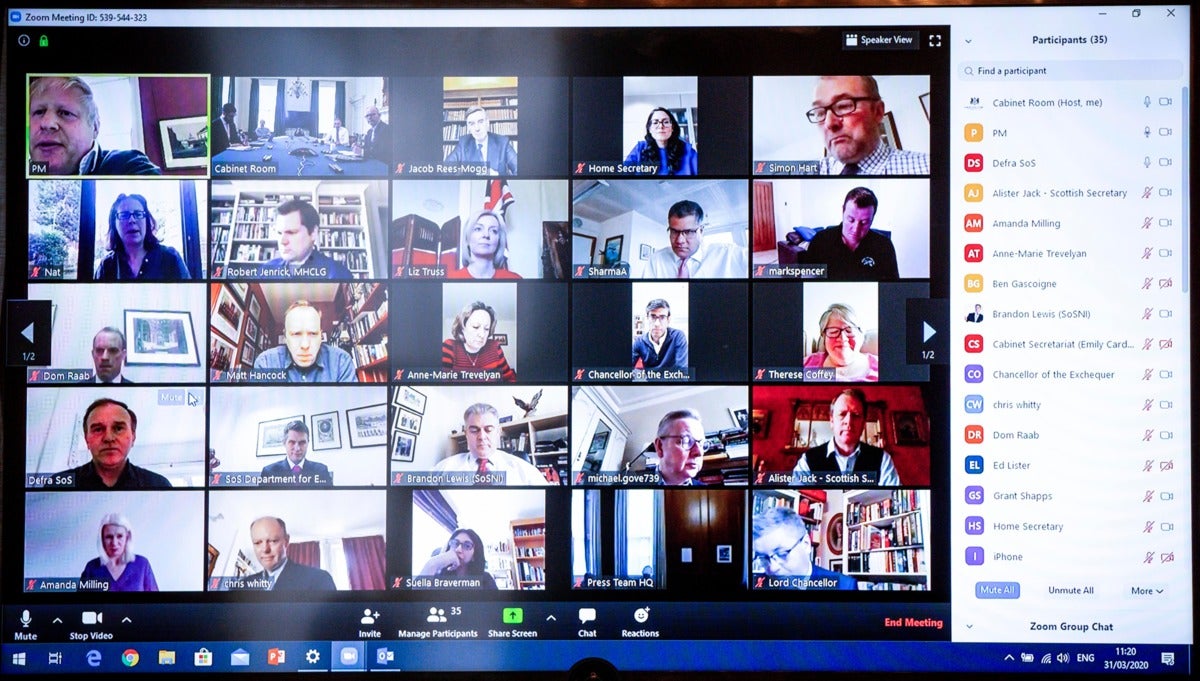
Even heads of state need some help with Zoom. A screenshot of a Zoom meeting shared publicly by the UK’s prime minister, Boris Johnson, included its Zoom Meeting ID. Don’t do that! Here’s why.
With more and more people using the convenient Zoom videoconferencing app to communicate while working from home, “Zoombombing” is becoming a thing. “Zoom bombing” is as bad as it would be in real life: When an uninvited guest suddenly shows up in your Zoom meeting and starts acting up, swearing, or sharing inappropriate pictures, everyone loses.
 Boris Johnson / Twitter
Boris Johnson / Twitter
Zoom in far enough, and you can clearly see the Zoom meeting ID in the upper left-hand corner of this Zoom meeting UK prime minister Boris Johnson shared on Twitter.
The first rule of Zoom meetings is the same as the first rule of Fight Club: Don’t talk about it. If you share a Zoom meeting link, it’s the same thing as telling your friends that your parents are away and you’re hosting a party Saturday night. If you’ve shared that link (or invitation) publicly on social media, the entire school will show up and trash your house. Or your meeting.
Boris Johnson broke the second rule of Zoom meetings: He shared the Personal Meeting ID. A PMI isn’t quite as bad as sharing the time and place of your rager. But sharing a PMI publicly is like sharing your home address: Any lowlifes know you’re hosting a party, just not when. In the case of Johnson’s cabinet meeting, this tells people that if they keep knocking at the door, they might get lucky.
By default, PMIs don’t change, and that’s why Zoom recommends against using it. “Avoid using your Personal Meeting ID (PMI) to host public events,” Zoom suggests. “Your PMI is basically one continuous meeting and you don’t want randos crashing your personal virtual space after the party’s over.”
Unfortunately, Johnson shared a screenshot of his Zoom screen on Twitter, with the PMI extremely visible in the upper left-hand corner. The Internet jumped all over it.
Johnson has more to worry about than just random yobs disrupting the call. As a head of state, there’s sure to be confidential information talked about that he doesn’t want made public.
Fortunately, Johnson (and Her Majesty’s Government’s IT staff) used two-factor authentication: while they publicly shared the PMI, they apparently at least secured it with a password, which can be configured in a number of different ways.
How to avoid Zoom bombing
Zoom’s blog post includes some handy tips to prevent strangers from barging into your group calls. There are actually a number of ways to secure your Zoom calls, providing that you actually enable them!
- Allow only invited guests. Exclusive parties (and Zoom calls) have guest lists. You can force Zoom invitees to log in with the same email you invited them with, essentially enforcing the invitation.
- No fashionably late guests. Did a guest show up early? Make them wait in Zoom’s Waiting Room, which also allows you to check them out and see if they’re legit before they’re allowed in. Once the guests have arrived, you can shut the door and lock the meeting, preventing any latecomers from arriving. Use the Participants window at the bottom of the screen for this.
- Keep ‘em in line. If you’re hosting a Zoom call, you can disable the video of individual participants, mute one or all of the participants, or even give them a time-out by placing them on a momentary hold, which disables their audio and video. Naturally, you can kick them out, too, using the Participants window and clicking on their thumbnail. If someone has learned their lesson, they can rejoin.
Hosts have the option of preventing guests from sharing their screens, and whatever memes (or worse) they have on it. Turning off file transfer prevents unwanted files from being shared with the rest of the video chat.
Did Johnson unwittingly unlock his government’s secrets? Probably not. But it’s an opportune time to point out that users, working from home with unfamiliar technology, are ripe for exploitation. Don’t be one of them.
