The conveniences of modern life also come with downsides. One drawback that can have an outsized impact on a person is digital stalking—the use of your digital footprint to keep tabs on you online and in the real world.
But you can take steps to minimize that risk. You don’t need to go to extreme lengths to maintain your privacy, either. Basic precautions will set you up well for the future, like turning off public sharing for social-media posts.
But you can go even further to increase your security measures to prevent cyberstalking—and most people concerned about digital stalkers will want to do so. Vulnerabilities can overlap. For example, social media can reveal facts that can make stalking you digitally and physically easier. And having the same user name across all apps and services could make finding you on the web and discovering one of your long-forgotten accounts with a weak password much simpler. (Both can lead to further intrusion into your life.)
This article breaks everything down for you, with bolded text that highlights key action items. Use it as a checklist to shore up your defenses.
Quick privacy tips
As you read through this article, you can use an incognito or private browsing window (right-click on these links and choose “Open link in incognito window” or “Open in private window”) if you feel that your computer might not be secure from an in-home threat.
Also, digital stalking can lead to real-world danger. If you believe you’re at risk, don’t stop after implementing these tips. Resources for people experiencing stalking, domestic abuse, and other violence exist, and you can consult with them and local groups (as well as local law enforcement or your national police force, e.g., the FBI) to get further help. And keep a paper trail if you believe someone is stalking and/or threatening you. Write down incidents of concern and take screenshots (or video) as much as possible.
Ways people can monitor your online activity
Your profile is set public
PCWorld
Your social media accounts or other apps and services may be broadcasting all of your posts or information for anyone to view. Remove the information or set your privacy level to friends-only (at minimum) to keep those deets away from prying eyes. Unfortunately, you can’t always predict which companies will do this, so you may have to comb through a lot of apps and websites for a thorough lockdown.
Also, when you’re tagged or otherwise named in other people’s public posts, someone can see into your life. You can change your settings to block others’ ability to tag you.
Your user name
Many people use the same user ID across all services. To avoid someone following you around the internet, mix it up. Use a unique login name for some services, if not all of them. If you use a password manager, you’ll be able to easily keep track of your user IDs.
Through your friends
Not only can other people’s public posts divulge specifics about your life, but your “friends” on websites or apps can also become a vulnerability. You won’t always know who they know, and what ends up getting shared indirectly.
You can minimize this risk by limiting your posts’ reach to trusted individuals, removing people you don’t know well from your friends list, and/or simply not sharing as much online.
Account infiltration

Soumil Kumar / Pexels
Another person can access your account if you have a weak, leaked, or shared password, or through any linked third-party services that have been compromised. Let’s say that you use Facebook to log into other websites. If someone gains access to your Facebook account, that could open up access to a ton of other sites as well.
At its most benign, you might find yourself with a freeloader on your Netflix account. But even in that case, that person can still see your viewing habits and some of your billing details, as well as your email address and possibly phone number, too. Such data can allow deeper digging into your life and snooping on personal messages or email if your security is weak overall. Your financial information, intimate conversations, and private photos could end up exposed.
To root out a spy, check your account activity. Many major services (Gmail, Facebook, etc.) show a list of IP addresses and the devices associated with them, as well as the time and date of the access. You can figure out your IP address by typing “what’s my ip” into Google or another search engine. (Your phone may have a different IP address than your PC if you use its cellular data connection.)
If you see any unknown IP addresses, log out that device or end its session. Also change your password as well to something strong and random. A password manager (even a good free one) will make that simple. Enable two-factor authentication to raise your security level even further, and limit third-party access to your accounts. Even if you don’t see any suspicious activity, you can still go through these steps to ensure you (and only you) have account access.
Physical access to your device(s)
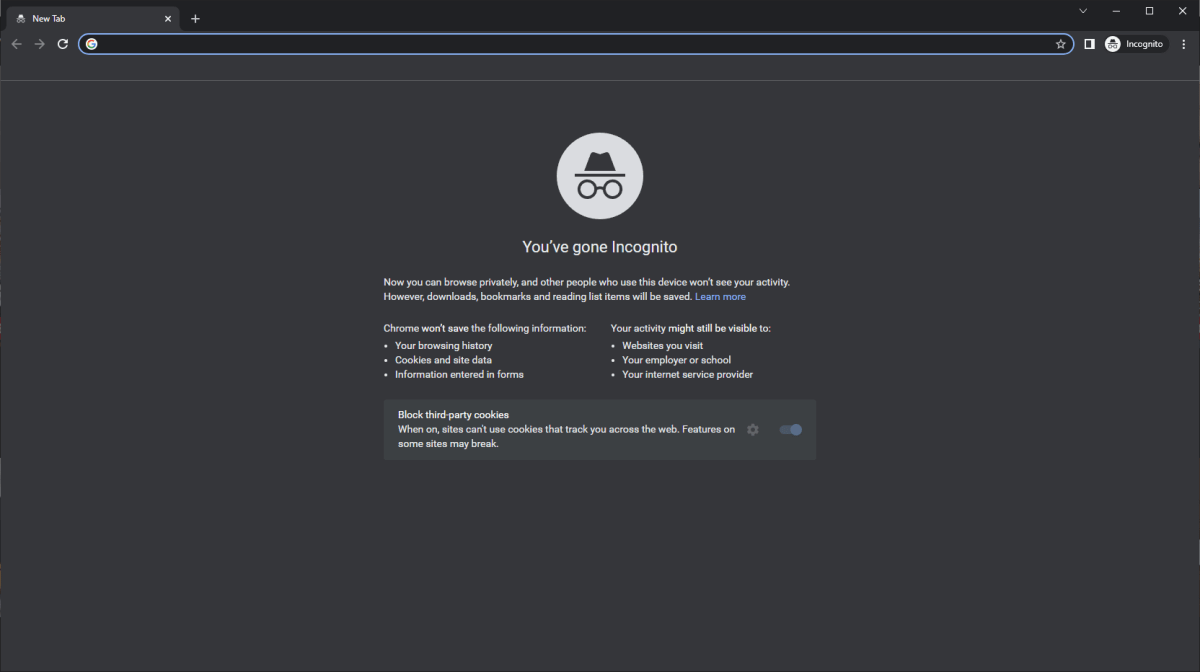
Incognito windows in Chrome are a way to keep people with access to your device from knowing your browsing history. The same mode exists in other browsers too but are named differently.
PCWorld
Checking IP addresses in your account activity will tell you when people outside your home are monitoring you, but not necessarily when someone inside your home is doing the watching. You might catch them that way on their own devices, but not when they use yours.
Maybe you don’t have a screen lock on your phone or an account password on your PC. Or perhaps you’ve shared that info in the past with a housemate, friend, or family member and never changed it. They can then have a look at any website or app you’re logged into. No need for the passwords to those accounts.
Keep people out by adding an authentication method to the device—or changing your existing credentials. If that’s not an option, log out of websites and applications when you’re not using them. For web browsing, you can also use an incognito window in Chrome, InPrivate window in Edge, or a private window in Firefox to avoid leaving a history of what sites you visit.
A private browsing session won’t prevent someone on your home network from being able to see your traffic requests, though. To cover that completely, you’ll need to use a VPN. Alternatively, you can use your phone’s cellular data connection.
Remote access to your PC
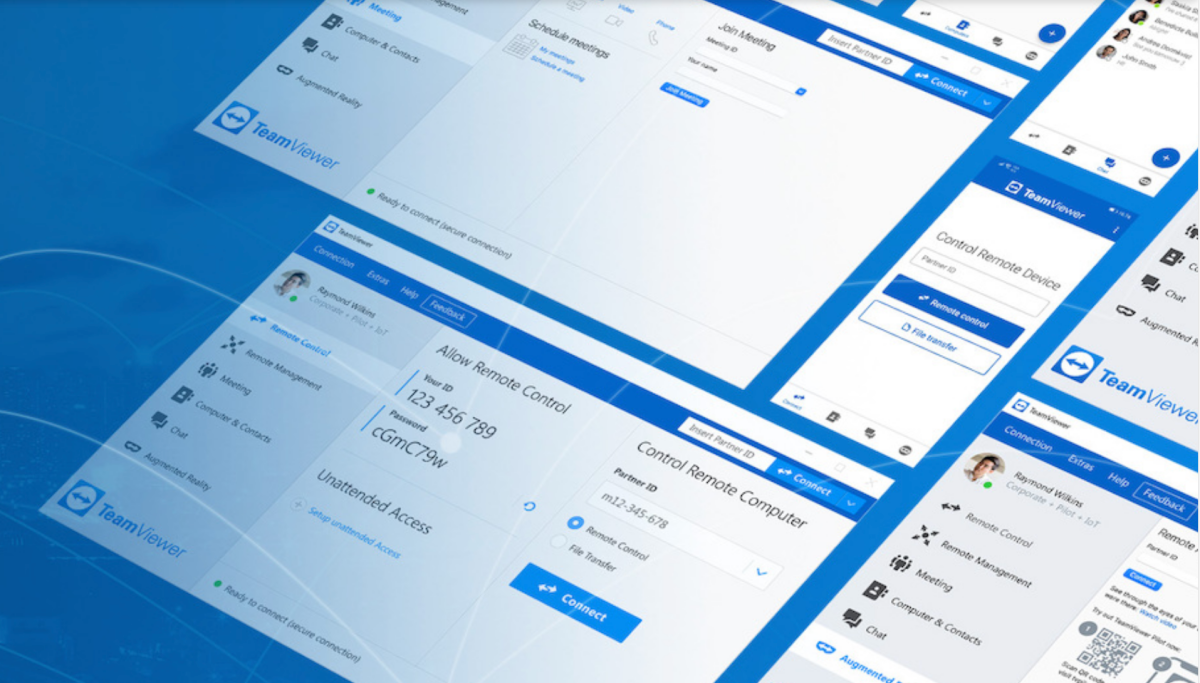
TeamViewer is a popular app that grants remote control of your computer to someone else.
TeamViewer
Checking account activity logs also won’t reveal if someone is monitoring you via remote access to your PC. It not only allows them to see everything you do in real time, but also control your computer.
If someone doesn’t have physical access to your devices, you’ll usually have to click a malicious link for them to gain remote access. So don’t click on any links you don’t recognize. Also run regular, thorough antivirus and antimalware scans on your PC. If you use Chrome, check your Chrome Remote Desktop settings as well to make sure no one has unauthorized access your PC. (And be sure that the Google account you use to sign into Chrome is secure.)
Someone with physical access to your devices may surreptitiously set up remote access software without your knowledge. One easy way to do this is turning on Remote Desktop, a feature built into Windows 10 Pro and Windows 11 Pro, or Apple Remote Desktop, the equivalent for macOS. Go into your settings to revoke access to unrecognized accounts or turn off the feature completely.
Third-party software alternatives for Remote Desktop and Apple Remote Desktop also exist. You can look for these by scanning through the installed apps on your PC. In Windows, type “Apps & features” into the Start menu or search bar, then start looking at the list of apps. On a Mac, open the Applications Folder. (Check both the one tied to the system, and the one tied to your user account.) Obvious remote-access software includes TeamViewer, but you can Google the name of any program you don’t recognize. Uninstall any monitoring apps that don’t belong on your system.
Ways people can monitor your physical location
You can leak information on your current physical location or even usual haunts through what you share online, either knowingly or not. Here’s how to plug that.
Social media
PCWorld
Public posts on Facebook, Twitter, and Instagram that tag or mention a location are a dead giveaway of where you’re at or where you like to visit. You can also give away your locale through sharing photos with landmarks or details recognizable to whomever is viewing the photo.
To solve this problem, lock down your posts. You can make your account private on Instagram and Twitter, and on Facebook, you can choose to limit who you share posts with. Make them Friends-only at minimum, or even more restricted if you’re connected to people you don’t know well. (You don’t know who they know, much less who may try to use them to get to you.)
Alternatively, you can just stop tagging or mentioning where you’re at. If you must, wait until after you’ve departed—and limit the habit to places you’re only visiting once, rather than spots you frequent. You can also change your settings to block others from tagging you in photos or locations by default.
Also be mindful of what you share. You’re not required to disclose your home address, workplace, education, or other identifying details. (You may need to share a phone number for two-factor authentication, but you can use a Google Voice number that can’t be easily traced to you.) Only reveal information when absolutely necessary and keep it as general as possible.
PCWorld
Photos
Photos shared online can betray your location in two ways. You have geotagging enabled for photos you take on your phone, or you’ve taken a photo with enough background details to reveal where you are. (Or both.)
You can either turn off geotagging entirely for your photos, or before posting a photo, run it through an app that strips its metadata (including location and the device used to take the snap). If you only need to remove location data, try Adobe Photoshop Express on Android; on iOS, try Snapseed. (Don’t reverse these recommendations, even though the apps exist for both platforms.) You’ll open your existing file, then save/export it. In your Photos app, you can look at the info of the copied photo to verify that the GPS data is gone.
As for what you take shots of, be mindful of what’s in the background behind you before you post a photo. You may not be able to eliminate all clues to where you are, though, so being careful about whom you share the photo with is also a strategy.
Other apps and services
Similar to social media, your settings in some apps and services can broadcast your usual haunts or habits. For example: Fitness apps that track your route when running or biking may make that public information by default. A travel app that blasts your itinerary to the wide internet. A calendar that’s set to public. Websites that allow anyone to see your wish lists and favorites.
Even Venmo can reveal the people who you interact with most, if you leave your transactions public—and if their settings are less lax than yours, it can again spill insight into your life you’d rather keep private.
Take the time to go through the settings of your apps and services. Verify that your details aren’t public at minimum, and consider locking down any extraneous information. Share only the minimum with friends as necessary (e.g., they probably don’t need to know your exact run route for fitness challenges, only that you did eight miles). To really go private, don’t neglect old accounts you use rarely or have abandoned.
Public record

Ethan Hoover / Unsplash
Your home address is easier to find than you might think. Past ones, too. At least, that’s true in the United States—even if you’ve never filed a change of address form with the U.S. Postal Service or bought a house, businesses you patronize may have shared your info with data brokers. That includes banks and other highly personal services.
Restricting this info can take a little elbow grease, but it is possible. First, perform a search on Google and other search engines for your name to see what kind of details immediately turns up. (You may need to add your location if you have a common name.) If you see any people-search sites come up (like whitepages.com, spokeo.com, etc.), look for your listing. If you find one, you can use the site’s opt-out process to get it removed.
Unfortunately, many people-search sites exist, and it can be a bit of a game of whack-a-mole trying to keep yourself off them. To reduce such work in the future, opt out of data sharing across all of the services you use, including financial institutions like banks. You generally can just call and talk to customer service to have this done. California residents should get a yearly notice that allows you to change your data-sharing preferences.
Domain registration
Do you have a website with your own domain? If your domain registrar doesn’t offer private registration (or you didn’t turn on the feature), your name, address, phone number, and email address can be found by anyone.
The fix is simple. If your registrar offers private registration, turn it on. Your registrar will substitute their own contact info for yours, and forward you any incoming messages from people trying to get in touch about your domain.
If your registrar doesn’t offer private registration, move to one that does. We have a curated list of the best domain registrars that you can reference.
Apple AirTags (and other Bluetooth trackers)

IDG
A Bluetooth tracker is a small physical object that can be placed on items to ensure they don’t go lost. That’s their intent, at least—but they can be used for stalking, too. Because the person would need to have access to your car, bike, bag, or other belonging, this form of monitoring your movements relies on at least an initial moment of close proximity.
Apple AirTags are the most potentially dangerous of the Bluetooth trackers, due to how many Apple devices are available for a tracker to ping off of and thus establish your location and route of movement. But Tile, Chipolo, and other trackers work in a similar fashion.
Our sister site Macworld has a full rundown of Apple’s steps to thwart stalking, as well as a guide on how to avoid being tracked via an AirTag. It explains in more detail how to use Apple’s built-in apps and tools to scan for trackers in your vicinity (even if you have an Android device). Tile also offers the ability to scan for unknown trackers, but not all other vendors do.
Unfortunately, you must have a smartphone or tablet in order to perform this kind of scan. Otherwise, you have to hope that you can hear an Apple AirTag’s beeping, which signifies a “lost” tag. Other Bluetooth trackers unfortunately do not have this feature.
If you have reason to believe someone might place a tracker on you, in your stuff, or on your car, you may want to begin regularly checking your stuff for anything that doesn’t belong.
Phone location
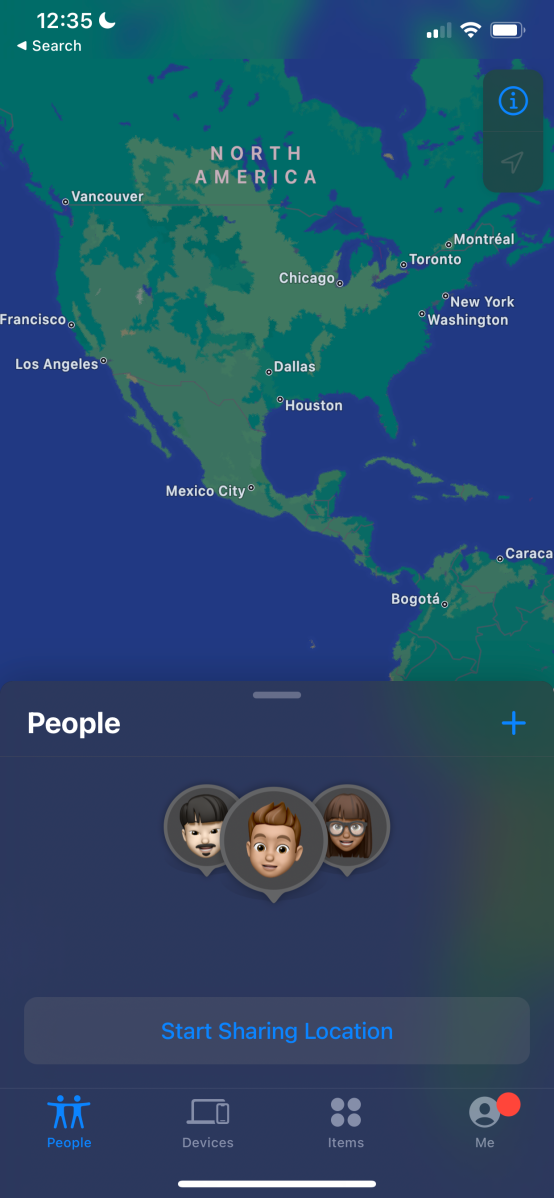
PCWorld
Your phone may be betraying your location to your friends and family—or anyone deemed as such in your settings.
If you have location settings on (this allows your cell phone to share your GPS location with apps, which is necessary when using a map app, ride sharing, or allowing an app to check into a place), it’s possible for select contacts to track you in real time if you allow it. In theory, only you should have control over this, but if someone has had physical access to your phone, they can grant permission to themselves or others too.
It’s a sword that cuts two ways: Useful if you need to keep track of your aging relative who sometimes gets lost going home on public transit, but dangerous if it’s a person who shouldn’t have that info.
On iPhone, you can check to see who has this level of access in your Find My app. On Android, sharing is done through Google Maps—click on your profile icon, then go to Settings > Location Sharing.


