Virtual private networks use slick marketing terms to charm potential users, but you can easily get tangled up when trying to pick it all apart. The language describing encryption methods is thick with acronyms and technical jargon, so searching cute phrases like “military-grade encryption” usually turns up more questions than answers.
But while the details of encryption can initially be confusing, things become pretty clear once you know how to sort out the information. Concepts like TLS, RSA certificates, keys, AES encryption, and the like will seem far less foreign, and it’ll be a snap to evaluate how worthy a VPN is of your attention. Here’s how to get there.
How VPN encryption works
Generally speaking, encryption is the process of converting data into code (an act known as encoding), which can then only be decoded by an authorized party. When your computer connects to a VPN, a multi-step encryption process should take place. The degree of security in each of those steps depends on the protocols used. Each protocol handles elements like authentication, key exchange, and encryption of the established connection in different manners.
You can usually break down modern VPN encryption protocols into these four parts:
- How the connection first begins (the “handshake”)
- How the connection generates the piece of code (“the key”) used to encrypt and decrypt data during the session (aka the key exchange)
- How long the encryption keys persist
- The encryption method used to protect the established connection
The protocols supported by a given VPN indicate the general level of encryption strength, but they can be configured to taste. Consequently, VPN services can use the same protocols but provide differing levels of security. One company may hew closer to industry defaults to boast faster speeds, while another might increase the key lengths/sizes used for encryption to maximize security.
How to untangle the specifics of VPN encryption
 PCWorld
PCWorld
Many VPNs support OpenVPN, a popular open-source protocol known for its high level of security.
Start by determining which protocols a particular VPN service supports. Currently, the industry favors three for their high security: OpenVPN, IKev2/IPSec, and Wireguard. You may also see proprietary riffs on known protocols, as well as slower or less secure ones like SoftEther, SSTP, and L2TP/IPSec. PPTP is rare these days, as it’s an old protocol and no longer provides adequate protection.
Next, dig up the details of how the VPN has configured its chosen protocols. Most services offer a nuts-and-bolts explanation in support pages, an FAQ, or blog posts. You should encounter terms like “RSA certificates” and “Elliptic Curve Diffie Hellman protocol” here. Online searching will clarify any terms you’re not familiar with.
Finally, take all the jargon that you’ve found and weigh it against industry standards. Again, online searching will help you fill in any knowledge gaps. Be wary of VPNs that don’t meet current industry defaults (e.g., 2048-bit keys for RSA certificates and 128-bit AES encryption). A VPN’s level of encryption should line up with its marketing claims, too—a provider that trumpets the iron-clad security but uses PPTP or even L2TP/IPSec gives reason for doubt.
As an example, here’s how we would go about interpreting HotSpot Shield VPN’s explanation of its encryption methods:
 PCWorld
PCWorld
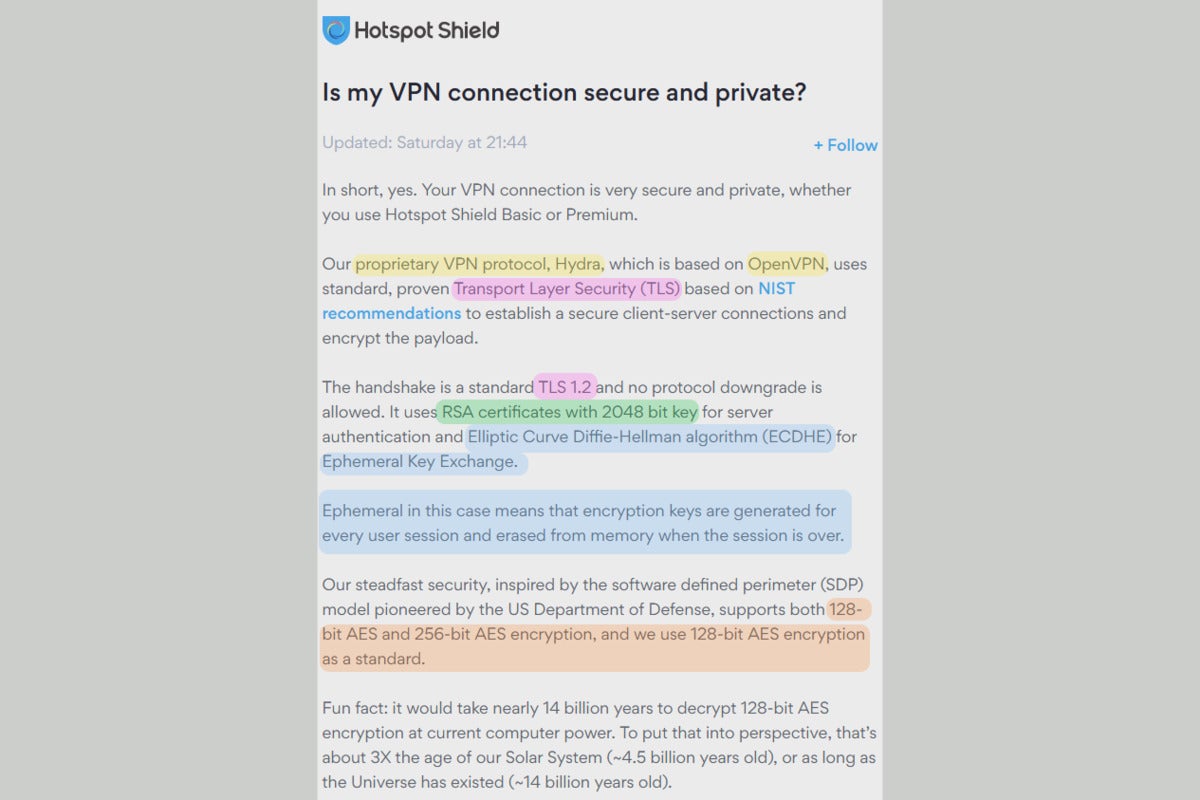
In this explanation of HotSpot Shield’s encryption configuration, the brightly colored highlights are what you need to figure out.
First, we’d identify supported VPN protocols. The key phrase here is “proprietary protocol based on OpenVPN.” That tells us that this company has taken one of the most secure VPN protocols and put their own spin on it. You’ll have to trust that it has implemented those changes well, since the code is not publicly available to review. (In contrast, OpenVPN is an open-source protocol.)
Next, we would puzzle out what function the remaining terms represent within the OpenVPN protocol. With a bit of work, it becomes clear that:
- TLS 1.2 relates to security at the start of a connection;
- RSA certificates are part of that encryption process;
- The Elliptic Curve Diffie Hellman algorithm then dictates how key exchange happens;
- That key exchange is an ephemeral exchange;
- The connection switches over to 128-bit AES encryption afterward. You can also configure your connection to instead use 256-bit AES encryption.
 PCWorld
PCWorld
Wikipedia has explanations for most encryption-related terms, but it can also turn into a rabbit hole in which you spend gobs of time unpacking the highly technical language.
To determine whether or not HotSpot Shield VPN has made smart choices for its setup, more research supplies further context:
- TLS 1.2: OpenVPN uses Transport Layer Security, or TLS, to secure the connection when it begins. Version 1.2 is considered the minimum default by experts. A newer, more secure version 1.3 exists as well but has not yet been as widely adopted.
- RSA certificates with 2048-bit key: TLS certificates rely on the RSA algorithm to keep data transmission secure. The minimum key length recommended these days is 2048-bit. Some VPNs use a longer key length (4096-bit), but the tradeoff is that it’s slower.
- Elliptic Curve Diffie Hellman algorithm: This protocol dictates how the piece of data (the key) used to encrypt and decrypt data routed through the VPN is generated. Like the RSA algorithm, ECDH relies on asymmetrical public-private key pairs but has different vulnerabilities. Its use following that of RSA certificates helps mitigate those weaknesses.
- Ephemeral key exchange: Unique keys are generated each session and then discarded, which reduces the chance of a third party obtaining the keys and thus decrypting your data.
- 128-bit AES and 256-bit AES encryption: 256-bit AES encryption is more complex than the 128-bit variety, which provides more protection against brute-force attacks, but it’s also slower. By choosing 128-bit AES encryption as the default for established connections but allowing 256-bit as an optional configuration, HotSpot Shield holds to industry standards while still giving users the choice to increase their level of security.
You would have to test a VPN to further verify it’s worth your time, but between online reviews and this research, you’ll go into the process well-informed. (In the specific case of HotSpot Shield, we’ve already done the reviewing for you.)
Overall, being able to perform this kind of check ensures that you can pass on any VPNs that don’t meet your standards.
Why so complicated?
Picking these details apart can take some time, which may be more than most people want to do. You can bypass this work by sticking to known services that are well-known and recommended by many experts in the field. We have our own list of VPNs that we’ve reviewed that you can reference, which includes providers like Mullvad, Windscribe, and HotSpot Shield. Opinions run rampant on forums and sites like Reddit, too.
