Mozilla has announced that its Firefox browser has begun to roll out encrypted DNS over HTTPS by default for all users in the U.S., a major step in the push to fully encrypt all Internet traffic and eliminate the risk of attack. However, while Mozilla is pushing the feature as “one of the many privacy protections you can expect to see from us in 2020,” it could be gearing up for a lengthy legislative battle.
On a technical level, DNS over HTTPS (DoH) encrypts the initial lookup of the website you want to reach, known as the Domain Name System. “DNS is a database that links a human-friendly name, such as www.mozilla.org, to a computer-friendly series of numbers, called an IP address (e.g. 192.0.2.1),” Mozilla explains. “By performing a ‘lookup’ in this database, your web browser is able to find websites on your behalf.”
Since these split-second requests also include your IP address, a hacker could take that information to create an online profile of you and the sites you visit, or the server itself could be collecting your data for advertising or marketing purposes, often without your knowledge.
By turning on default DNS over HTTPS, Firefox assures users that it is only using trusted servers—Cloudflare and NextDN at the outset—which are “committed to throwing away all personally identifiable data after 24 hours, and to never pass that data along to third-parties.” So if you use the Firefox browser in the U.S., your Internet traffic will ignore your ISP’s server and redirect it to either Cloudfare or NextDN to ensure encryption from start to finish. It’s somewhat like surfing through a VPN without actually signing into one.
The battle over encryption
However, while end-to-end encryption might sound like something everyone should want and need, not everyone is on board. The reason why default DoH is limited to the U.S. is because of the UK’s own efforts to block child porn and other sites at the request of the government. Default DoH would make it much more difficult for ISPs to implement such filters.
 IDG
IDG
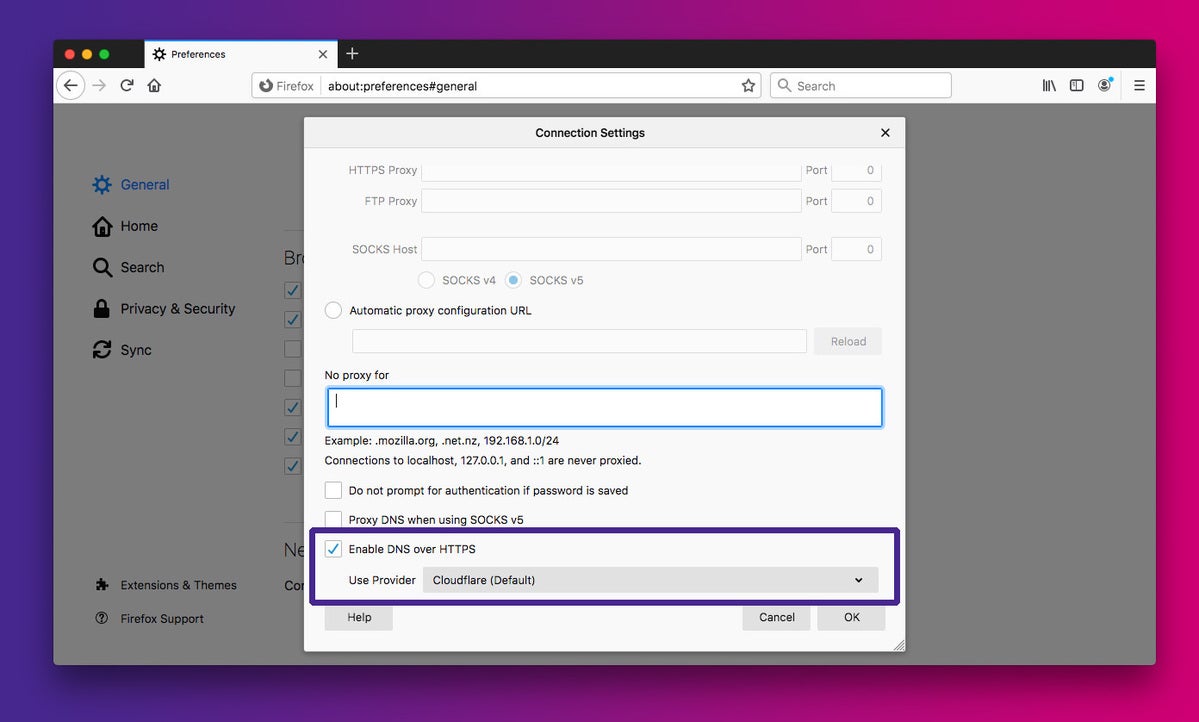
You can enable or disable DNS over HTTPS in Firefox’s Network settings.
DoH is also offered on the Chrome, Opera, and Edge (Chromium) browsers, but it’s not turned on by default and not all that easy to implement. Apple’s Safari browser does not yet offer a DoH option.
The U.S. government is also wary of DNS over HTTPS. Google’s Chrome browser—which offers DoH as an option but not a default—came under fire last year by the House Judiciary Committee “because of concerns that it could give the company a competitive advantage by making it harder for others to access consumer data,” according to The Wall Street Journal. Additionally, cable and telecom ISP providers are also concerned that DoH will break “critical internet features and functionality,” including parental controls, and “undermine federal government and private sector efforts to use DNS information to mitigate cybersecurity risks.”
For its part, Mozilla downplays any potential risk and vows to work with companies, schools, and other organizations, as well as ISPs to mitigate concerns over DoH. In a statement to ZDNet, the company said it was “We’re surprised and disappointed that an industry association for ISPs decided to misrepresent an improvement to decades-old internet infrastructure.”
To use default DoH, you need to update or download the latest version of the Firefox browser (73.0.1). Users can disable default DoH on the Firefox browser—or enable it if you’re outside the U.S.—by visiting the Network tab under General settings and unchecking the Enable DNS over HTTPS box.
